cbox
-
Posts
6 -
Joined
-
Last visited
XSChris's Achievements

Apprentice Grade 1 (2/44)
1
Reputation
-
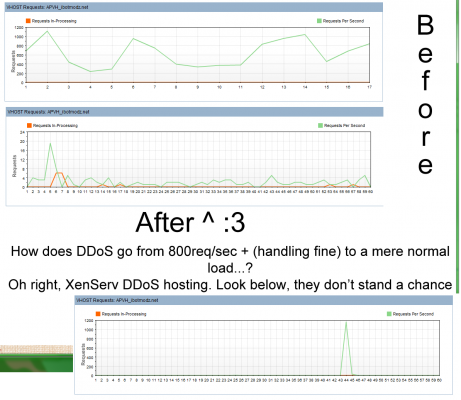
Whoever "was" attempting to rape bandwidth, I kick ass and chew bubble gum, and I'm all outta gum
- Show previous comments 1 more
-
 well...... IVE GOT BALLS OF STEEL.
well...... IVE GOT BALLS OF STEEL. -
 well.... He has quotes from 80s movies (They Live, and the proper quote is "I have come here to chew bubblegum and kick ass.... And I'm all out of bubblegum.)
well.... He has quotes from 80s movies (They Live, and the proper quote is "I have come here to chew bubblegum and kick ass.... And I'm all out of bubblegum.) -
 yeah, the original quote is from They Live, not dukenukem. he just butchered it.
yeah, the original quote is from They Live, not dukenukem. he just butchered it.